Hi Folks,
I know it’s a little bit lame to mention 2 clickjacking vulnerabilities in row but that what bug hunters always do exposing the largest companies security failures, (Previously was Telegram) this time is the gigantic well-known 19 billion dollar messenger WhatsApp.
WhatsApp Inc., was founded in 2009 by Brian Acton and Jan Koum, both former employees of Yahoo!. After Koum and Acton left Yahoo! in September 2007, the duo traveled to South America as a break from work. At one point they applied for jobs at Facebook but were rejected. For the rest of the following years Koum relied on his $400,000 savings from Yahoo!. In January 2009, after purchasing an iPhone and realizing that the seven-month-old App Store was about to spawn a whole new industry of apps, he started visiting his friend Alex Fishman in West San Jose where the three would discuss “…having statuses next to individual names of the people,” but this was not possible without an iPhone developer, so Fishman introduced Koum to Igor Solomennikov, a developer in Russia that he had found on RentACoder.com. Koum almost immediately chose the name “WhatsApp” because it sounded like “what’s up”, and a week later on his birthday, on February 24, 2009, he incorporated WhatsApp Inc. in California. However, early WhatsApp kept crashing or getting stuck and at a particular point, Koum felt like giving up and looking for a new job, upon which Acton encouraged him to wait for a “few more months”
Regarding the vulnerability, Clickjacking is one of the oldest web application typical vulnerabilities where (by design) a lot of companies never paid attention to it.
Clickjacking, also known as a “UI redress attack”, is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the the top level page. Thus, the attacker is “hijacking” clicks meant for their page and routing them to another page, most likely owned by another application, domain, or both.
Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of stylesheets, iframes, and text boxes, a user can be led to believe they are typing in the password to their email or bank account, but are instead typing into an invisible frame controlled by the attacker.
What an attacker can do with a clickjacking on WhatsApp?
1. Sending a messages in behalf of the currently logged in users
2. Deceive users to create unwanted chat groups, make calls, add contacts, block contacts, etc…
Back to January 2015, One of Seekurity members reported the vulnerability to Facebook (because at this time WhatsApp was one of Facebook’s acquisitions) and here’s a screenshot of the original report.
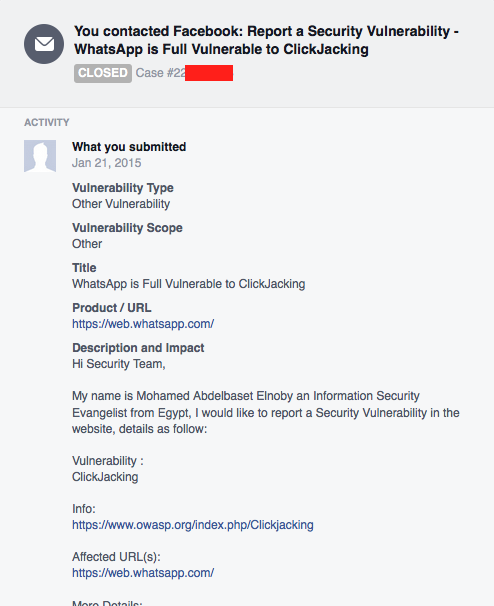
WhatsApp Report to Facebook
The whole web client of WhatsApp was vulnerable to clickjacking attack, Sometimes web applications with a minimal functionalities are immune to vulnerabilities because of the fact that you’re attacking just a few features!
Encryption and Web Clients!
Both Telegram and WhatsApp are supporting end-to-end encryption but the fact is when the client fails to protect it’s users the crypto means nothing!
Unlike Telegram and it’s tricky UI protection mechanisms, WhatsApp was totally vulnerable without an Iframe busting techniques or even an X-FRAME-OPTIONS header value!
When it comes to a web app with a few features to attack, Attackers are looking for any ways that gives them an access to such hard-to-hack services and regardless that a clickjacking attack might be worthless “sometimes” but in our case it still effective!
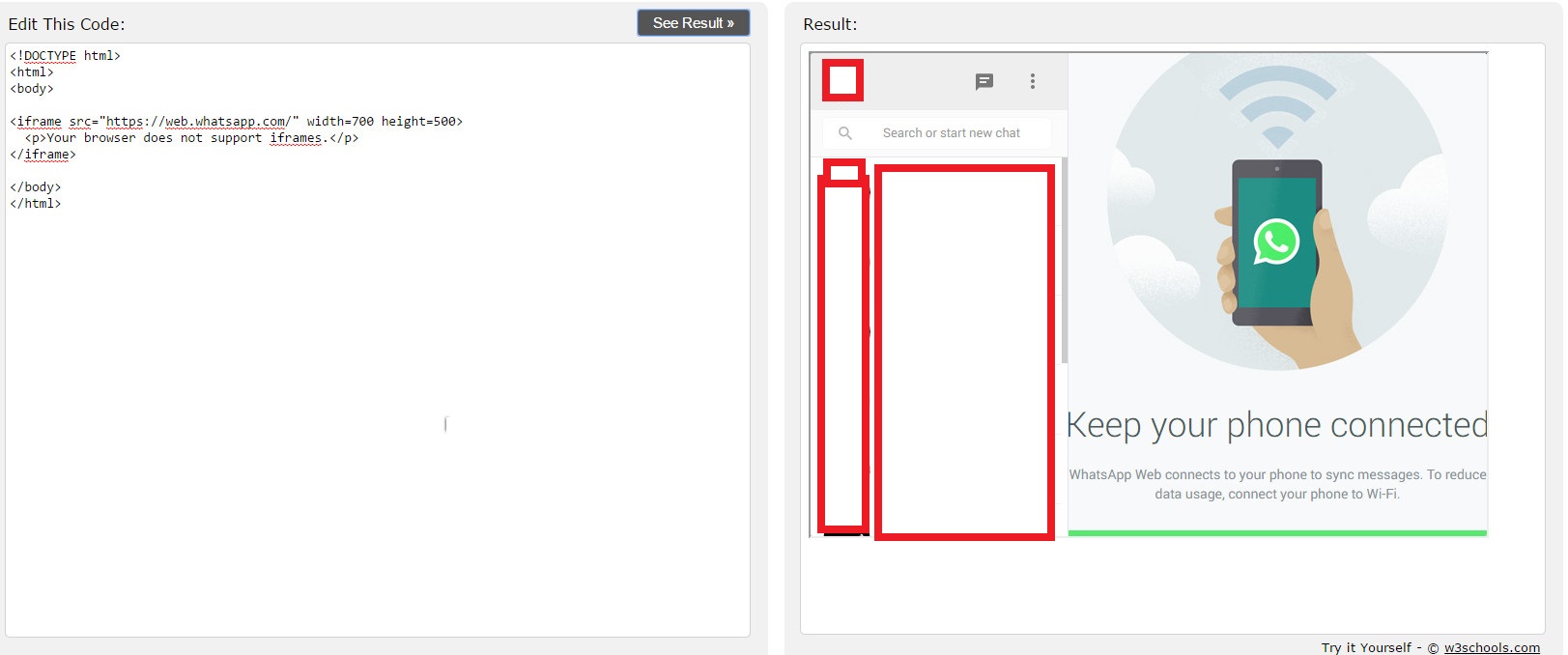
WhatsApp ClickJacking PoC Demonstration and PoC Code
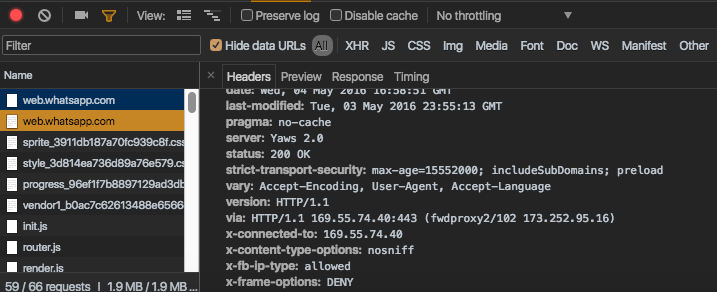
The Fix:
WhatsApp finally noticed the risk of the issue and fixed it by applying an X-Frame-Options header with a value of “Deny”
Hey!
Building a website? Or already built a one? Think twice before going public and let us protect your business!
Article image credits: (deccanchronicle.com)
another ClickJacking client failure! Vulnerability web WhatsApp WhatsApp Clickjacking Vulnerability - Yet another web client failure! Yet

Previous Next