Hi Folks,
Days ago, one of our clients received an email with the next subject in Spanish: “Problemas con tu membresia de Netflix” (Problems with your Netflix membership).
The email was in his SPAM folder with the follow caption: “Be careful with this message. It contains a suspicious link that has been used to steal people’s personal information. Unless you trust the sender, don’t click on links or reply with personal information.”
Thanks Google SPAM filters! But we aren’t sure if the rest of email service providers can flag the email as SPAM, maybe not because Google has a powerful spam filter. The first time we took down the malicious site, it appeared again in a few hours.
Here is what we found:
Phishing objective
Obtain your:
-
- Netflix account: Email & password.
-
- Personal data: Complete name, birthday, billing address, city, state.
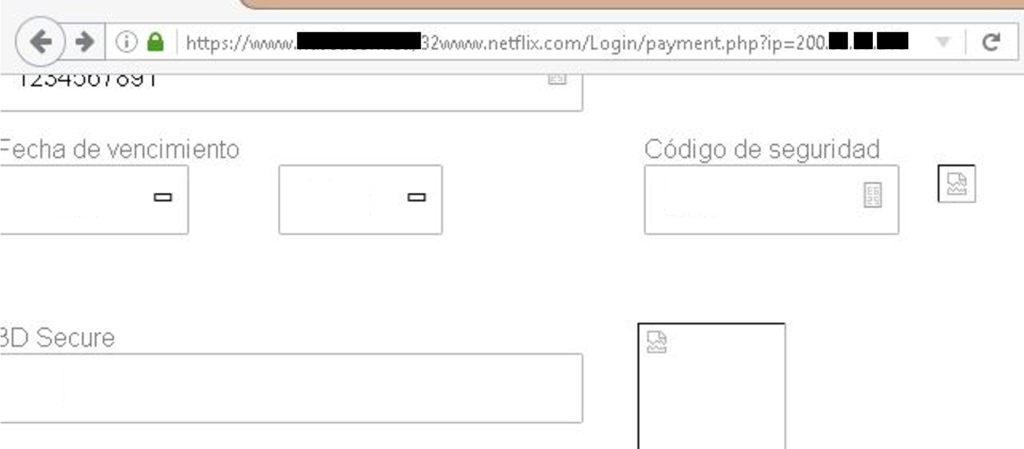
- Credit Card data: Name, CC number, due date, security code, 3-D Secure code and your account number.
- IP Address
This is how the email looks:
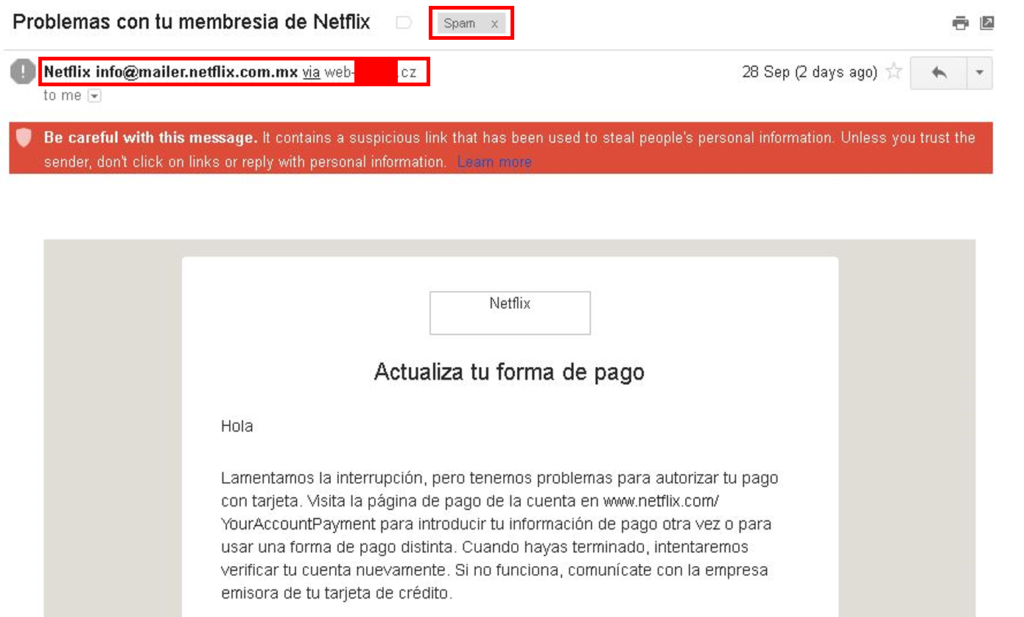
…we have problems to authorise your payment. Visit payments page [Malicious link] … enter your payment information again …
Taking a look of the email headers
PHPMailer was used to send the email, one of the advantages using this technology is the Integration with SMTP without a local mail server, send emails with multiple TOs, CCs, BCCs and REPLY-TOs and more…
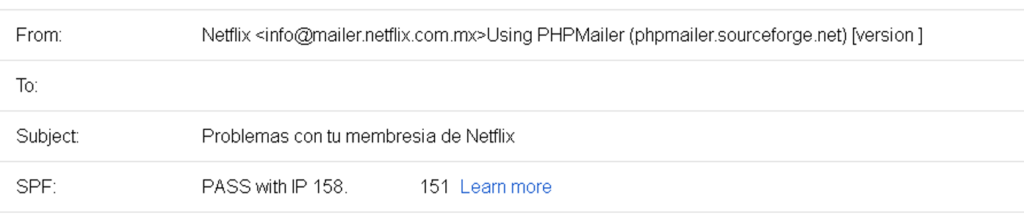
The sender e-mail address info[
Fortunately, the Google’s Sender Policy Framework (SPF) flagged the IP as SPAM.
The e-mail sender is masked, the real one is miklos[@]XXXXXXX[.]cz from an university located Czech Republic.
The phishing website
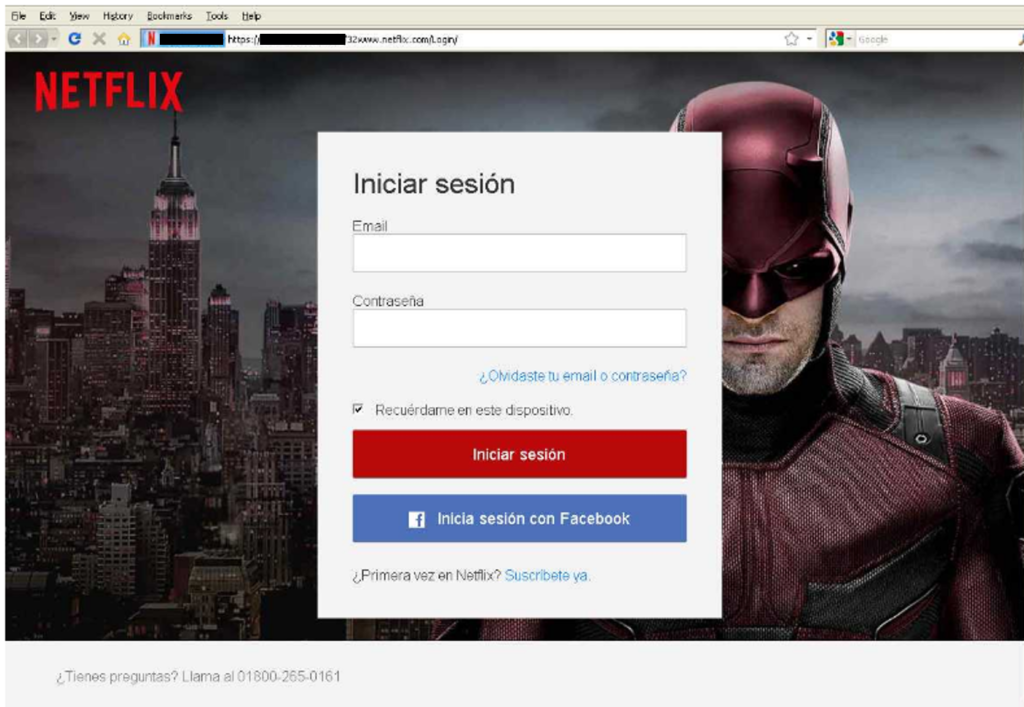
The phishing website looks so real, but in the URL you can notice that the URL of this website is long and the first part has words not related to Netflix Domains or SubDomains.
Following the HTTP transactions
Before reach the final website, we travelled around the whole world, across USA, Netherlands and Australia.
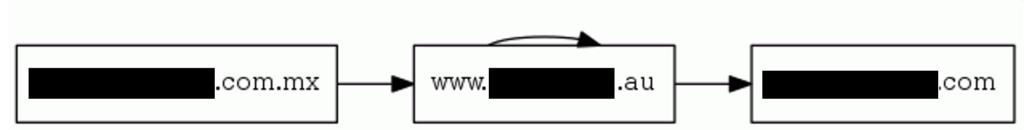
The first website is from a Mexican company hosted in USA, their site was compromised and the “bad guys” installed a JavaScript what redirects you to another website from an Australian company.
The Australian website (with ‘au’ Domain) contains the phishing website and it makes 2 GET Request to an IP located in USA to get the Daredevil Image for the background and the Netflix icon.
Tracking
- Orange: Email’s origin
- Blue: Redirections
- Red: Phishing hosting
![]()
Let’s Login!
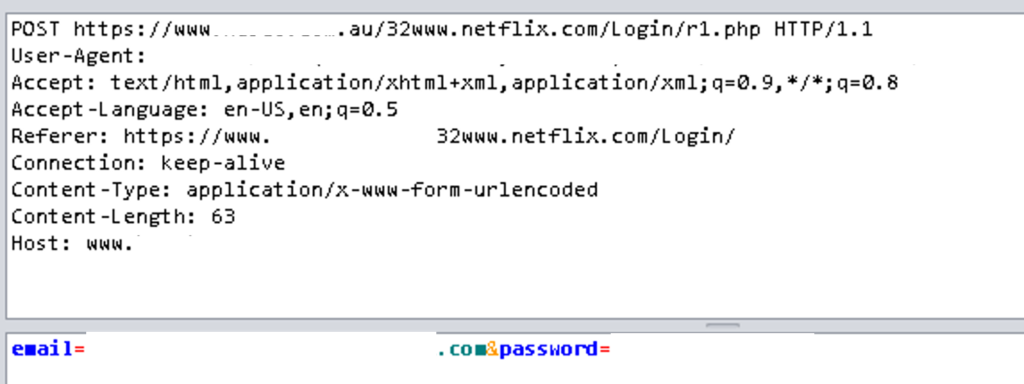
Login request
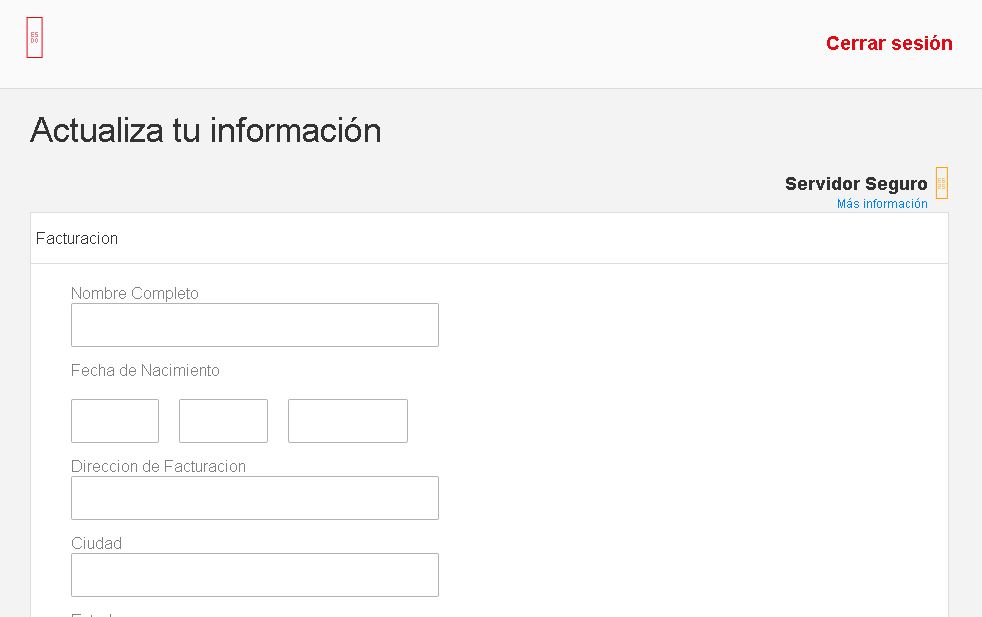
After introduce the e-mail and the password required by the main page, it shows us another screen, who’s asking for update our personal data.
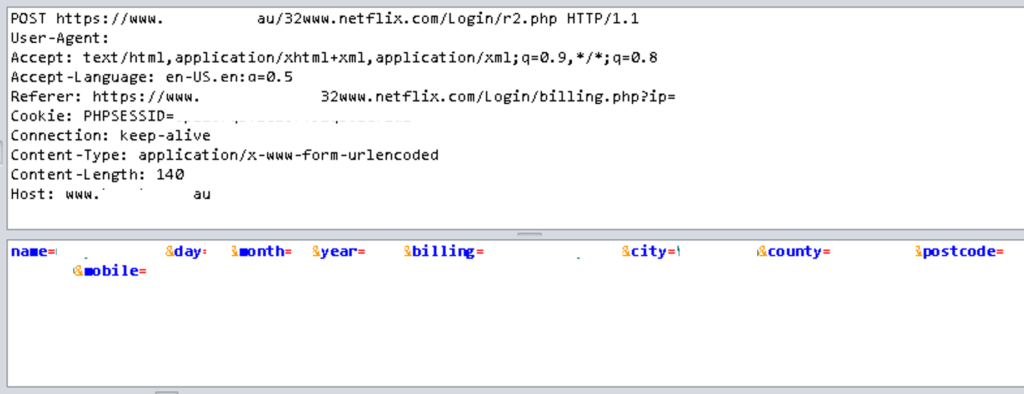
Clicking “next” button, the next page ask for the Credit Card data
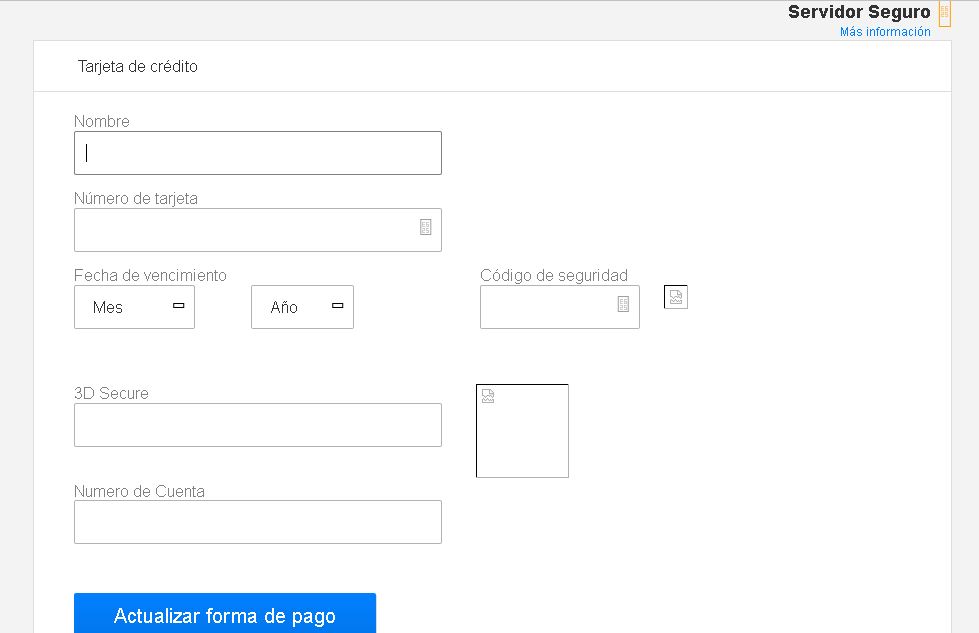
At the end of the URL we noticed our IP, that indicates they are tracking the users.
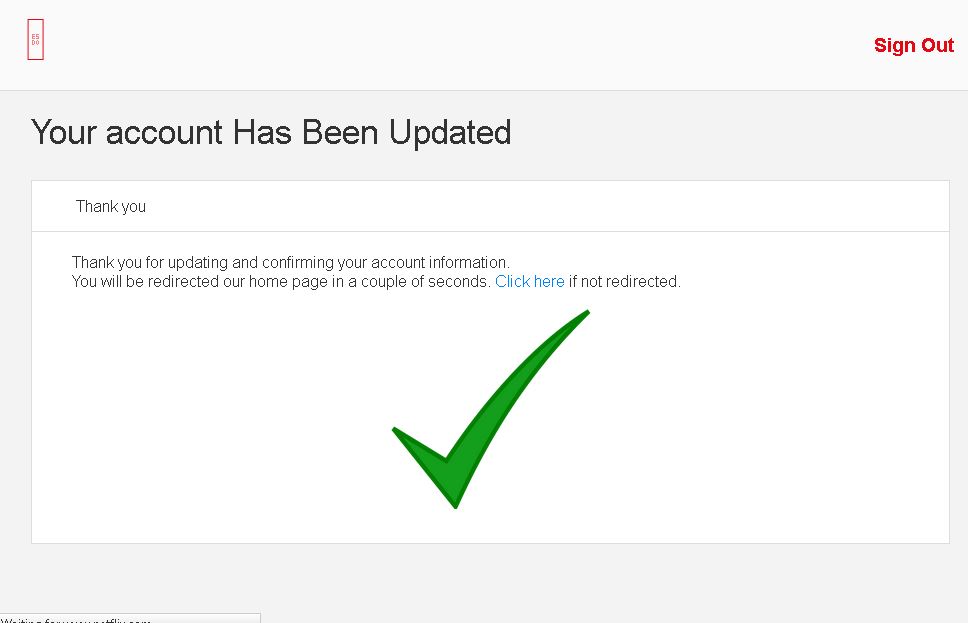
The last page is the confirmation: Your account has been updated! :D!
Going deep: Extracting the source code
A simple script used to redirect the traffic to the Australian server from the Mexican website.

The email and password are sent to the r1.php file and personal data is sent to the r2.php file.
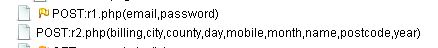
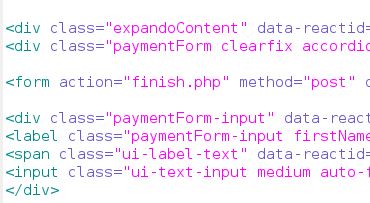
The Credit Card data is submitted by a POST request to the ‘finish.php’ file.
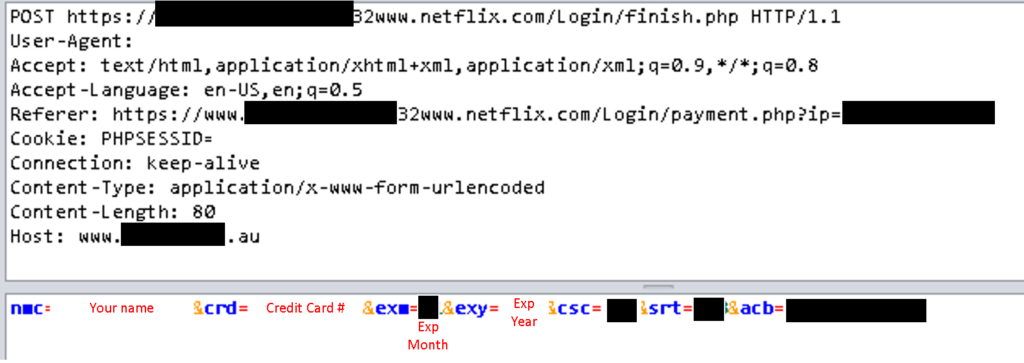
Finally, after submit your data the site redirects you to the real Netflix page.
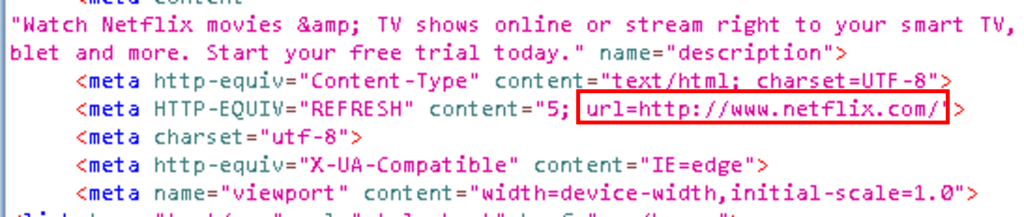
We couldn’t find any record in the servers, this type of phishing sends the data to the attacker email address after pressing the submit button.
Thanks to the admins who helped us to take down this attack.
Some recommendations
- Before introduce any data in an website, verify the URL is from the real company.
- Verify the sender e-mail address.
- Ask in the social networks of the company about the e-mail, they can help you to verify if is real or not.
- Most of the companies never ask for credit cards data vía email.
Hey!
Building a website? Or already built a one? Worried about your security? Think twice before going public and let us protect your business!

Previous Next